The POP3 access for Windows Live ID is finally here. I have tried configuring my Outlook Client with the POP3 settings of Hotmail. Check out the screenshots below for configuring Outlook to connect with Windows Live POP3.
1. Open Outlook
2. If a account is already configured then, click on Tools > Account Settings > Email > New. Else you would be prompted to configure Outlook when you open it.
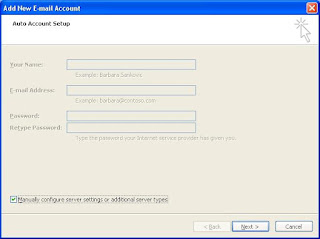
3. Select “Manually Configure Server Settings or Additional Server Types” and then click on next.
4. Now you would see the following 3 options, click on Internet E-mail and then click on next to configure the POP3 Account

5. Now configure the Outlook Client with the below mentioned details

The POP3 Settings would be:
Account Type : POP3
POP3 Server : pop3.live.com
SMTP Server : smtp.live.com
Email Address : Your hotmail email address
Password : Your password for the hotmail ID

Then click on More Settings and then on “Outgoing Server” tab. Check “My Outgoing Server (SMTP) requires authentication” and then select “Use same settings as my incoming mail server”
Now the final step, click on Advanced, then check “The Server requires an encrypted connection(SSL)”.
Incoming server (POP3) = 995
Outgoing Server (SMTP) = 25
Select “TLS”, under, “Use the following type of encrypted connection”

Now click on OK and then complete the wizard or if you want you can click on “Test Account Settings” and the account is configured.
I hope that this helps… :)
Source : http://mailcall.spaces.live.com/blog/cns!CC9301187A51FE33!49799.entry
STEP 1:
Once the machine is powered on, it goes through a POST (Power-On Self-Test) sequence. The POST sequence displays information about the BIOS, and the amount of memory installed. The system will also attempt to initialize PCI cards. Once the POST sequence has completed, one can then see a basic table outlining the system configuration including disk information, and PCI card information.
STEP 2:
The system goes through the process of acquiring a DHCP address, normally referred to as DORA:
DHCP (D)iscover
DHCP (O)ffer
DHCP (R)equest
DCHP (A)cknowledge
If the system is able to acquire an IP Address successfully, then the networking configuration settings are populated, such as Default Gateway, DNS Servers, WINS servers and so on.
If the system is not able to acquire an IP Address, then the system will time out / fail trying to process various networking functions - including the application of group policies and even possibly logging on to the client machine.
STEP 3:
Let’s assume that the system has received an IP address from the DHCP server, now the DHCP Client service will try to register its IP Address with the DNS Server
STEP 4:
The system attempts to query DNS for a SRV record for a Domain Controller. If the system locates a domain controller it then begins the process of applying system-level domain and group policies.
If no DC can be located, then we are in another timeout situation where group policies will fail to apply.
STEP 5:
Once the computer settings are applied, the user logon prompt is displayed and the user enters their credentials
STEP 6:
If the system was able to contact a domain controller, then the logon is authenticated and user policies are applied. If the system was not able to contact a domain controller, the system may log the user in with cached credentials. Since no domain controller could be located, user GPO’s will not be applied.
Troubleshooting Boot-up Issues:If there is any issues while booting the system, you can to boot the computer in a "Clean Boot" Mode and check if the issue still persists:For a clean boot, please try these steps:
-Click on start, then click on run (if run is not available, incase of Windows Vista, then type run, in the start search box and hit enter).
-On the run window type "msconfig" (without quotes)
-Click on services tab, click on "hide all microsoft services", now click on disable all
-Click on startup tab, click on disable all
-Click on OK and restart the computer
One can also try to boot the computer in Windows Safe Mode, to diagnose the issue, to boot the computer in safe mode, While booting the computer keep tapping the "F8" key on the keyboard, till you see "Advanced Boot Options" and then using the arrow keys highlight "Windows Safe Mode" and then hit Enter.
Automatic Rebooting
The goal of Windows Update is to always keep your computer as safe and secure as possible. Therefore, if you decided that Windows Update should Install updates automatically, an automatic system reboot may be a part of the process. Choosing any other option will disable automatic reboots, but we do recommend that you keep automatic updates enabled!
Why does Windows Update sometime require a reboot? Well, some updates require access to files currently in use by your system. Windows Update does not know if or when those files will be available to use, so your system requires a reboot to avoid any conflicts. For security-related updates, your computer is unsafe before that reboot occurs: it is vulnerable to attacks which exploit the issue(s) fixed by the update requiring a reboot.
For that reason, when Windows Update automatically installs an update that needs a reboot, it proceeds with an automatic reboot. In order to make the updating process more convenient for you by preventing disruptions to your work, WINDOWS UPDATE defaults to installing updates (and subsequently rebooting your computer) at 3:00AM. Additionally, if updates are installed while you happen to be using the computer, and a reboot is required, Windows Update notifies you with this dialog:
The center countdown timer starts at 5 minutes. You can Restart now, or Postpone the reminder by 10 minutes, 1 hour, or 4 hours (In Windows XP, you can postpone for 10 minutes).
There is one exception – a system administrator can deny your rebooting privileges. For user accounts without rebooting privileges, Windows Update disables the Postpone button. You can Restart now, or your system will automatically reboot after 5 minutes.
Update Deadlines
A system administrator can configure some computers behind a Windows Server Update Services (WSUS) server with update deadlines. When reaching a deadline, Windows Update begins an automatic install of those updates based on settings determined by the system administrator.
This deadline-based automatic install behaves identically to a Windows Update automatic install. Therefore, if one or more of the deadline updates requires a reboot, Windows Update presents the same dialog box to you with the same options and conditions.
Policies to Change Automatic Rebooting Behavior
Two group policies allow you to configure how Windows Update handles automatic reboots. In order to edit these policies, you must own Windows XP Professional, Windows Vista Business, or Windows Vista Ultimate. The Group Policy Editor is not available in Home Windows versions.
To use the Group Policy Editor, follow these directions for both Windows XP and Windows Vista: http://support.microsoft.com/kb/307882
In Windows Vista, there is another way to access the Group Policy Editor:
· Click Start
· Select Control Panel
· Type Group Policy into the search box
· Click Edit Group Policy, the only result that appears
Once inside the Group Policy Editor:
· Expand Local Computer Policy
· Expand Computer Configuration
· Expand Administrative Templates
· Expand Windows Components
· Finally, select Windows Update.
The Group Policy Editor with related Windows Update policies looks like this:
With Automatic Updates enabled, the two following policies help you configure automatic reboot behavior.
No auto-restart with logged on users for scheduled automatic updates installations
If you set this policy to Enabled, then your system will never automatically reboot when a user is logged on to it. After Windows Update automatically installs updates that require a reboot, it presents all logged-on users with the following dialog box:
With this policy Enabled, Windows Update never automatically reboots your system, so there is no 5 minute timer. You can Restart now, or Postpone the reminder by 10 minutes, 1 hour, or 4 hours (In Windows XP, you can postpone for 10 minutes).
Not Configured is the default policy setting and uses the 5 minute timer. Disabled works identically to the Not Configured setting.
Delay Restart for scheduled installations
This policy allows you to change the initial timer for automatic reboots. If you set this policy to Disabled or Not Configured, the default setting, then Windows Update uses the default wait time of 5 minutes. However, if you set the policy to Enabled, it asks you to enter a number which sets the initial wait time.
For example, if you set the number to 15, Windows Update presents the following dialog after it finishes automatically installing an update that requires a reboot:
Notice how the text following “Restarting in:” began with a 15 minute timer instead of a 5 minute timer. Other behavior remains the same.
There are a lot tools available to help you set up Windows Update to act how you want it to.
|
There are cases when you run out of disk space in your system drive, and you desperately need to increase it. Uninstalling applications and deleting old files can be a start, but you might also need some quick disk space injection.
I run into this situation when I recently reformatted my home computer. They usually come from factory with only one partition, and you need to keep data and system files in the same volume (argh). The first thing I do when I put my hands on a new computer is to create separated volumes for system and data. But this time I miscalculated how much space my system drive would need, and I quickly run out of disk space in my C: drive.
I see some people disabling restore points to release disk space. Unless you’re really, really sure of what you’re doing, don’t do that! There are a couple of things you can do to release space quickly without having to take such drastic measures:
Option 1: Delete old restore points
One thing you can do to release disk space is to delete old System Restore and Shadow Copies. If you read this blog, you know I’m a System Restore super fan and I’m by no means suggesting that you disable System Restore. But if your system is stable, and you’re sure you won’t need any recent restore points, you can do the following:
1. Run Disk cleanup, and wait for it to calculate disk space.
2. In the second tab, More Options, under System Restore and Shadow Copies group, click Clean up. Vista will ask you if you’re sure. Be sure you’re sure, because this operation is not undoable.
Option 2: Resize your System Restore Points allocated size
If you’re interested in changing your System Restore allocated size, you can run the command (from an elevated command prompt)
vssadmin resize shadowstorage /on=D: /For=D: /MaxSize=10GB
In the case above, I was changing shadowstorage for my D: drive. Replace D: for your own system
drive letter.
Please consider that you might lose some older restore points if you decide to decrease allocated disk space. Also, if you allocate a space that is too small, you might not be able to save any restore points at all, and that would be the same as having it completely disabled. Be careful when reducing your System Restore Points allocated size.
Microsoft Internet Security and Acceleration (ISA) Server Best Practices Analyzer Tool
The ISA Server Best Practices Analyzer is a diagnostic tool that automatically performs specific tests on configuration data collected on the local ISA Server computer from the ISA Server hierarchy of administration COM objects, Windows Management Instrumentation (WMI) classes, the system registry, files on disk, and the Domain Name System (DNS) settings. The resulting report details critical configuration issues, potential problems, and information about the local computer. By following the recommendations of the tool, administrators can achieve greater performance, scalability, reliability, and uptime.
Microsoft Exchange Best Practices Analyzer v2.8The Exchange Server Best Practices Analyzer programmatically collects settings and values from data repositories such as Active Directory, registry, metabase and performance monitor. Once collected, a set of comprehensive ‘best practice’ rules are applied to the topology. Administrators running this tool will get a detailed report listing the recommendations that can be made to the environment to achieve greater performance, scalability and uptime.
See the Exchange Team blog for more info on the Exchange 2007 Readiness Check: http://msexchangeteam.com/archive/2006/07/28/428506.aspx. Additional Exchange Analyzer tools are available here.
SQL Server 2005 Best Practices AnalyzerThe SQL Server 2005 Best Practices Analyzer (BPA) gathers data from Microsoft Windows and SQL Server configuration settings. BPA uses a predefined list of SQL Server 2005 recommendations and best practices to determine if there are potential issues in the database environment.
Microsoft Best Practices Analyzer for Windows SharePoint Services 3.0 and the 2007 Microsoft Office SystemThe Microsoft Best Practices Analyzer for Windows SharePoint Services 3.0 and the 2007 Microsoft Office System Best Practices Analyzer programmatically collects settings and values from data repositories such as MS SQL, registry, metabase and performance monitor. Once collected, a set of comprehensive ‘best practice’ rules are applied to the topology. Administrators running this tool will get a detailed report listing the recommendations that can be made to the environment to achieve greater performance, scalability and uptime.
Microsoft Forefront Client Security BPA
The FCS Best Practices Analyzer Tool is designed for administrators who want to determine the overall health of their Forefront computers and to diagnose current problems. The tool scans the configuration settings of the computer and reports issues that do not conform to the recommended best practices.
Office Communications Server 2007 Best Practices AnalyzerThe Microsoft Office Communications Server 2007 Best Practices Analyzer Tool is a diagnostic tool that gathers configuration information from a Microsoft Office Communications Server 2007 environment and determines whether the configuration is set according to Microsoft best practices. You can install the tool on a client computer that runs Microsoft .NET Framework 2.0, or on a server that runs Office Communications Server 2007.
Windows Small Business Server 2003 Best Practices AnaylzerThis tool examines a server that is running Windows Small Business Server 2003. The tool collects configuration information from many sources including the following sources:
- Active Directory Windows Management Instrumentation (WMI)
- Registry
- Metabase
Then, the tool analyzes the collected information, and the tool verifies this information for correctness. After the tool has collected and analyzed the information, the tool presents a list of issues that are sorted by severity. For each issue, the tool provides descriptions of what the problem is and of how you can fix this issue.
Best Practice Analyzer for ASP.NETThe Best Practice Analyzer ASP.NET (alpha release) is a tool that scans the configuration of an ASP.NET 2.0 application. The tool can scan against three mainline scenarios (hosted environment, production environment, or development environment) and identify problematic configuration settings in the machine config or web config files associated with your ASP.NET application. This is an alpha release intended to gain feedback on the tool and the configuration rules included with it.
BizTalk Server 2006 Best Practices AnalyzerThe BizTalk Server 2006 Best Practices Analyzer performs configuration-level verification by reading and reporting only. The Best Practices Analyzer gathers data from different information sources, such as Windows Management Instrumentation (WMI) classes, SQL Server databases, and registry entries. The Best Practices Analyzer uses the data to evaluate the deployment configuration. The Best Practices Analyzer does not modify any system settings, and is not a self-tuning tool.
Microsoft System Center Mobile Device Manager 2008 Resource Kit - Best Practices AnalyzerMDM Best Practices Analyzer (BPA) Tool helps you to analyze the prerequisites for MDM setup and deployment. Because each MDM server component has different prerequisites, the tool helps you to plan and build a successful deployment environment by assessing each server's readiness for MDM before you run MDM Setup. In addition to analyzing each server's individual readiness, BPA Tool helps you to verify the firewall configuration that MDM requires between servers running MDM Device Management Server and servers running MDM Gateway Server. Finally, after you deploy MDM, you can run a post-deployment scan to help make sure your installation works properly and follows MDM best practices.
Microsoft Commerce Server 2007 Best Practices Analyzer
The Microsoft Commerce Server Best Practices Analyzer performs configuration level verification, by reading and reporting only. For example, the Best Practices Analyzer gathers data from Windows Management Instrumentation (WMI) classes, Microsoft SQL Server databases, registry entries, IIS Metabase Settings, and other parts of your deployment, and uses the gathered data to determine whether best practices are being followed. The Best Practices Analyzer does not modify any system settings, and is therefore not a self-tuning tool.
Visual Studio Team System 2008 Team Foundation Server Power Tools with TFS BPAThe Visual Studio Team System 2008 Team Foundation Server Power Tools is a set of enhancements, tools and command line utilities that improve the Team Foundation Server user experience. This download includes Best practice analyzer for TFS along with other important tools
Group Policy Diagnostic Best Practice Analyzer for Windows Server 2003 (32 bit and 64 bit Editions)
The Microsoft Group Policy Diagnostic Best Practice Analyzer (GPDBPA) for Windows XP and Windows Server 2003 is designed to help you identify Group Policy configuration errors or other dependency failures that may prevent settings or features from functioning as expected.
In SBS 2008 we have centralized the location of log files, all log files will now be placed in C:\Program Files\Windows Small Business Server\Logs. From a support perspective this is a big plus in simplifying troubleshooting as you will always know where the log file will be located. We have compiled a list of important logs and their associated wizards below.Please note that you will also find many event log (*.evt) files in the SBS log directory. These files are a snapshot of the event logs at the completion of the SBS install.

Microsoft Hyper-V Server 2008 is a great choice for customers who want a basic and simplified virtualization solution for consolidating servers as well as for development and test environments. Hyper-V Server 2008 only offers the most basic of virtualization features, making it ideal for:
- Test and Development
- Basic Server Consolidation
- Branch Office Consolidation
- Hosted Desktop Virtualization (VDI)
Customers who require richer and more robust virtualization features, such as Quick Migration, multi-site clustering, large memory support (greater than 32 GB of RAM), and more than four processers on the host server, should use Windows Server 2008. Windows Server 2008 provides business continuity, disaster recovery, greater scalability for consolidating large workloads, and flexible and cost-effective virtualization rights (one free virtual instance for Standard Edition, four free virtual instances for Enterprise Editions, and unlimited virtual instances for Datacenter Edition with the purchase of a license of Windows Server 2008).
APIs, Specifications, and How-To
-
NEW! Microsoft Hyper-V Server 2008 Getting Started Guide-
NEW! Microsoft Hyper-V Server 2008 Configuration Guide-
Hypervisor Functional Specification—Hyper-V Hyper call API-
Virtualization WMI ProviderVirtual Hard Disk Image Format Specification-
Performance Tuning Guidelines for Windows Server 2008 Webcasts
-
Momentum Webcast: Virtualization Capabilities of Windows Server 2008 (Level 100)-
Momentum Webcast: Are You Ready for Virtualization? (Level 200)
1. Open the Registry Editor click on the Start button on your taskbar, then click on Run and type "regedit" and click on OK to start the regedit utility.
2. Expand HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer
3. Create a new key called "DriveIcons". Under this key, create a new key with the letter of your drive.
4. To change the icon for that drive, create a key inside that one called "DefaultIcon" and set the path of (Default) to the location of your icon.
Example: C:\DefaultIcon\
then (Default) = E:\Icons\IconName.ico
Copy/Paste the following code in Notepad And then Save it as .reg
Then double click on it to merge it with the regisrty
::::::::::::::::::::::::::::::::::::::::CODE::::::::::::::::::::::::::::::::::::::
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Registry Editor]
@="Your Name Or Name of the Application"
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Registry Editor\command]
@="Location Of The Application"
The Notification Area holds a past items list for Applications that once appeared on the notification area.As you can see in the screenshot below the past items are full of apps and programs which were runned quite some time ago. For instance the activation item which I ran the same day Vista was installed.
These items can be cleared by editing the following registry keyCode:
[HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\TrayNotify]IconStreams and PastIconsStream
To clear the past items do the following:
- Browse to the registry keyHKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\TrayNotify
- Then rename the key's IconStreams and PastIconsStream to IconStreams_2 and PastIconsStream_2
- Create 2 new Binary key's called IconStreams and PastIconsStream and give them the default value.
- Now delete the first 2 key's IconStreams_2 and PastIconsStream_2 (the ones you renamed)
- All you have to now is reload the registry by logging off and on or restart Windows Vista.After this the list should be blank and cleared.



